How BIG's Blockchain Works: Crypto Tech Explained
Blockchain 101: The Tech Behind BIG
Blockchain technology is a distributed ledger system that enables secure, transparent, and immutable record-keeping across a network of computers. At its core, blockchain consists of blocks of data linked chronologically in a chain, with each block containing transaction records that are verified through cryptographic methods rather than by a central authority.
The relationship between blockchain and BIG cryptocurrency is fundamental, as BIG operates on a public blockchain network. This underlying technology provides BIG with security features, decentralization advantages, and transparency capabilities that distinguish it from traditional financial systems. Unlike conventional databases managed by a single entity, BIG's blockchain distributes data across a global network of nodes, making it resistant to censorship, fraud, and single points of failure.
Inside BIG: Core Components That Power the Network
The distributed ledger technology (DLT) that powers BIG blockchain functions as a synchronized database replicated across multiple locations. Unlike traditional systems where a central administrator maintains records, BIG's DLT ensures that every network participant has access to an identical copy of the ledger, creating unprecedented transparency and accountability.
BIG utilizes the Proof of Stake (PoS) consensus mechanism to validate transactions and secure the network. This process involves network participants (validators) collaborating to verify transactions, with successful validators receiving newly minted BIG tokens or transaction fees as incentives. This mechanism ensures network security and integrity while preventing double-spending and fraudulent transactions.
Smart contracts within the BIG cryptocurrency ecosystem are self-executing agreements with the terms directly written in code. These contracts automatically execute when predetermined conditions are met, enabling trustless interactions without intermediaries. In BIG's network, smart contracts facilitate automated transactions, decentralized applications (dApps), and programmable token functionalities that enhance the versatility and utility of the ecosystem.
The structure of BIG's blockchain technology consists of interconnected blocks, each containing a cryptographic hash of the previous block, a timestamp, and transaction data. This design creates an immutable chain where altering any information would require consensus from the majority of the network, making BIG's blockchain highly resistant to tampering and manipulation.
Myths vs Reality: Common BIG Blockchain Misconceptions
One common misconception about BIG's blockchain network is that it is completely anonymous. In reality, BIG offers pseudonymity, where transactions are publicly visible but not directly linked to real-world identities. This distinction is important for users concerned about privacy, as transaction patterns can potentially be analyzed to identify users.
Regarding technical limitations, many newcomers believe that BIG's blockchain technology can process unlimited transactions instantly. The truth is that BIG currently handles a finite number of transactions per second, which is less than some traditional payment processors. The development team is addressing this through scaling solutions and protocol upgrades scheduled for future network updates.
Energy consumption is another widely misunderstood aspect of BIG cryptocurrency. Unlike energy-intensive mining blockchains, BIG employs a Proof of Stake consensus mechanism that requires significantly less energy. This results in a carbon footprint much smaller than traditional banking systems or other cryptocurrencies.
Security concerns often stem from misconceptions rather than actual vulnerabilities. While critics claim BIG's blockchain network is susceptible to hacking, the network has maintained robust security with no successful attacks on its core protocol. The majority of security incidents involving BIG have occurred at user wallets or third-party services, not within the blockchain itself.
Getting Started with BIG's Blockchain (Easy Steps)
Interacting with BIG's blockchain technology begins with setting up a compatible wallet. Users can choose from official desktop wallets, mobile applications, hardware wallets, or web-based interfaces depending on their security needs and convenience preferences. Once set up, users can send, receive, and store BIG tokens while directly connecting to the blockchain network.
For those looking to explore BIG cryptocurrency blockchain more deeply, recommended tools include blockchain explorers for tracking transactions, development frameworks for building applications, and test networks for experimenting without using real tokens. These resources provide invaluable insights into the inner workings of the blockchain and allow for hands-on learning without financial risk.
New users should follow essential best practices, including backing up wallet recovery phrases, using strong, unique passwords, enabling two-factor authentication when available, and verifying all transaction details before confirming. Additionally, starting with small amounts and gradually increasing engagement as comfort grows can help mitigate potential losses while learning.
For comprehensive educational resources, market insights, and detailed guides on BIG's blockchain network, visit MEXC's Knowledge Base. MEXC offers beginner-friendly tutorials, advanced technical analyses, and regular updates on BIG's development.
Key Takeaways: What Makes BIG's Tech Special
BIG's blockchain technology combines distributed ledger technology with advanced cryptography to create a secure and transparent system for digital transactions. This architecture enables BIG cryptocurrency to offer unique advantages over traditional financial systems. Ready to apply this knowledge? Check out our 'BIG Trading Complete Guide' for practical trading strategies and step-by-step instructions.
Popular Articles

What is Solana Mobile (SKR)?A Blockchain-Native Smartphone Platform Bridging Hardware, dApps, and Tokenized Governance
Key Takeaways1)Solana Mobile is a hardware-first Web3 platform, integrating self-custody and blockchain security directly into smartphones.2)Saga and Seeker phones function as on-chain access devices,

What is Immunefi(IMU)? A Complete Guide to Web3's Leading Security Platform
Key Takeaways1) Immunefi focuses on continuous Web3 security coordination, not one-time audits.2) Bug bounties and audit competitions form the core of its security model.3) Magnus serves as an operati

What Is VOOI ($VOOI)? A Non-Custodial Perpetual DEX Aggregator Explained
Key Takeaways1)VOOI is a non-custodial perpetual DEX aggregator that routes trades across multiple DEXs without holding user funds.2)The platform leverages chain abstraction and intent-based execution

Balancing Security and Accuracy: Dynamic Logic of Risk Control Systems
As crypto markets evolve, so do the tactics used by fraudsters and market manipulators. To keep users safe and preserve market integrity, crypto exchanges must constantly enhance their risk control an
Hot Crypto Updates

hadtotakeprofits sir (HTTPS) Spot Trading Platform Comparison: Why MEXC Leads the Market
Choosing the right hadtotakeprofits sir (HTTPS) spot trading platform can significantly impact your trading success. MEXC stands out among cryptocurrency exchanges with superior features, competitive

Hadtotakeprofits sir (HTTPS) MEXC Spot Trading App: Your Gateway to Mobile Trading
The MEXC spot trading app revolutionizes how you trade hadtotakeprofits sir (HTTPS) with industry-leading zero maker fees and access to over 3,000 trading pairs. As one of the world's most trusted cry

hadtotakeprofits sir (HTTPS) Spot Trading Strategies: A Beginner's Guide
Spot trading involves buying and selling cryptocurrencies for immediate delivery at current market prices. For beginners looking to trade hadtotakeprofits sir (HTTPS), understanding effective spot tra

hadtotakeprofits sir (HTTPS) MEXC Spot Trading Fee: Complete Guide for Beginners
Understanding MEXC spot trading fees is crucial when trading hadtotakeprofits sir (HTTPS). MEXC operates on a maker–taker fee structure with 0% fees for makers and 0.05% fees for takers on spot market
Trending News

Wall Street bank JPMorgan says stablecoin market could grow to $600 billion by 2028
Markets Share Share this article Copy linkX (Twitter)LinkedInFacebookEmail Wall Street bank JPMorgan says stablecoin ma

Vertical Aerospace Progresses Towards Full Piloted Transition Flight
Full-scale prototype completes ten flights as part of transition programme Majority of the transition envelope successfully expanded UK Civil Aviation Authority
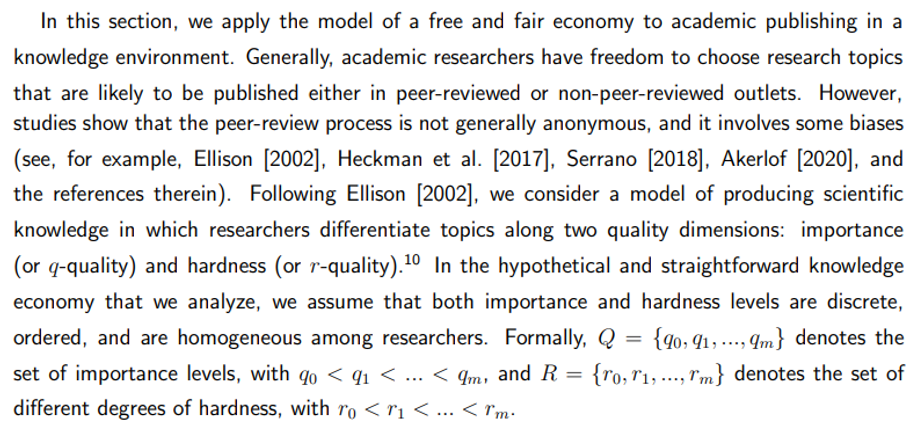
Academic Publishing and Fairness: A Game-Theoretic Model of Peer-Review Bias
Exploring how biases in the peer-review system impact researchers' choices, showing how principles of fairness relate to the production of scientific knowledge based on topic importance and hardness.

Vitalik sold KNC and STRAYDOG tokens in exchange for 15,916 USDC.
PANews reported on December 19 that on-chain data shows that Vitalik Buterin's nominal address vitalik.eth just sold 29,500 KNC (approximately $6,000) and 30.5
Related Articles

What is Solana Mobile (SKR)?A Blockchain-Native Smartphone Platform Bridging Hardware, dApps, and Tokenized Governance
Key Takeaways1)Solana Mobile is a hardware-first Web3 platform, integrating self-custody and blockchain security directly into smartphones.2)Saga and Seeker phones function as on-chain access devices,

What is Immunefi(IMU)? A Complete Guide to Web3's Leading Security Platform
Key Takeaways1) Immunefi focuses on continuous Web3 security coordination, not one-time audits.2) Bug bounties and audit competitions form the core of its security model.3) Magnus serves as an operati

What Is VOOI ($VOOI)? A Non-Custodial Perpetual DEX Aggregator Explained
Key Takeaways1)VOOI is a non-custodial perpetual DEX aggregator that routes trades across multiple DEXs without holding user funds.2)The platform leverages chain abstraction and intent-based execution

Balancing Security and Accuracy: Dynamic Logic of Risk Control Systems
As crypto markets evolve, so do the tactics used by fraudsters and market manipulators. To keep users safe and preserve market integrity, crypto exchanges must constantly enhance their risk control an
