At the time of writing, there is not much activity, and there is no information about investments. Points can be earned at three levels: as an ambassador, as a regular user, and as a project builder. We are also waiting for the launch of the main points program for everyone.
Follow the project on social media so you don’t miss any important updates.
Highlights:
- we perform tasks;
- farm points.
If you have any questions during the activities, you can ask them in our Telegram chat.
Useful links: Website | X
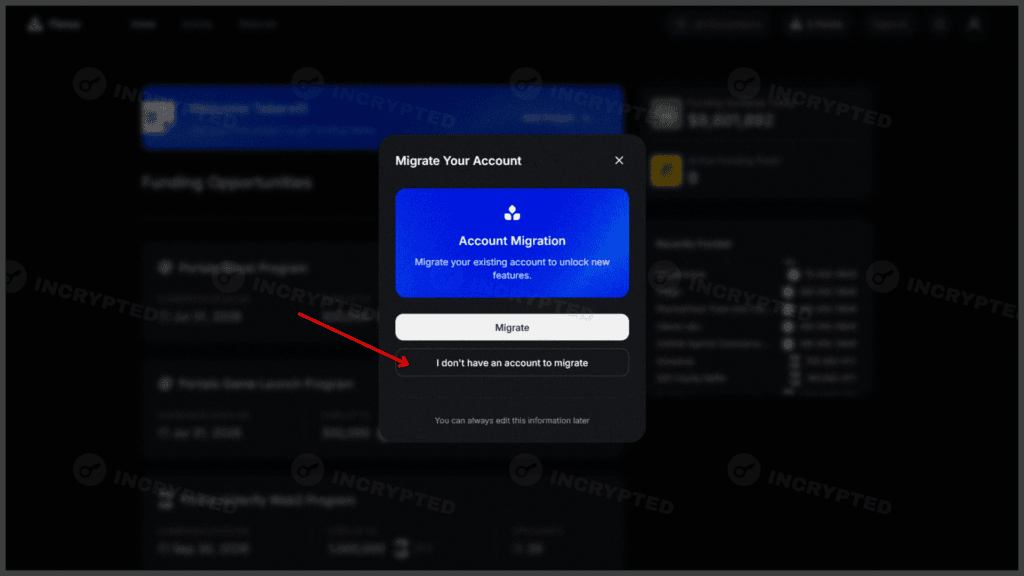 We are going through registration. Data: Thrive.
We are going through registration. Data: Thrive.
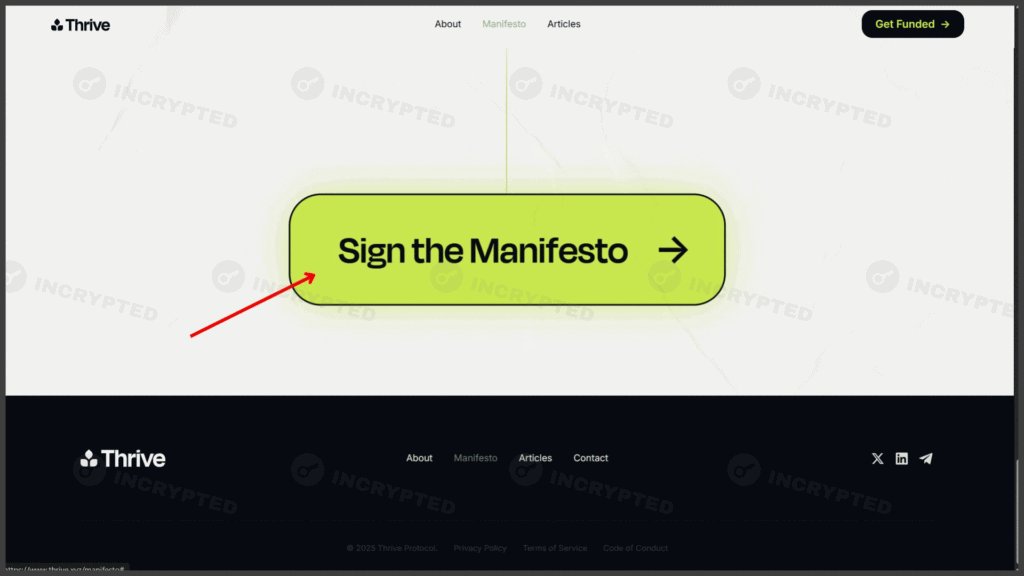 Signing the manifesto. Data: Thrive.
Signing the manifesto. Data: Thrive.
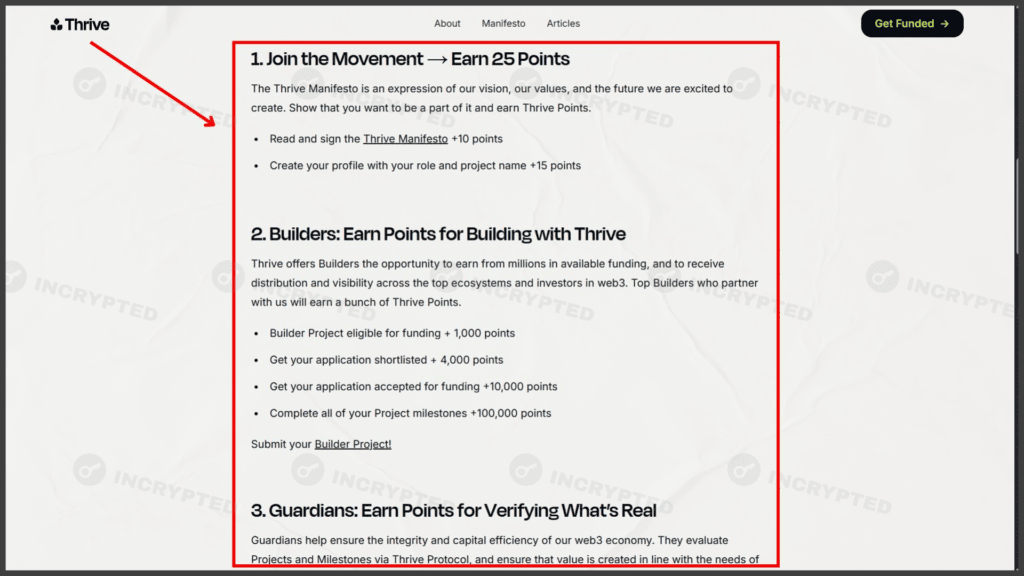 Additional tasks. Data: Thrive.
Additional tasks. Data: Thrive.


