In this article:
• 1. Guide to completing the activities
• 2. Conclusion
Thrive Protocol is a platform for distributing grants in Web3 based on the Proof of Value model, where funding is only issued after real value has been confirmed.
Recently, the team launched the Thrive Season 1 campaign, where you can farm points for a potential drop.
In this guide, we will take a closer look at the activity and show step-by-step actions on the platform.
- Go to the website and register. In the pop-up window, click I don’t have…, select a role, connect your social networks, and fill out your profile:
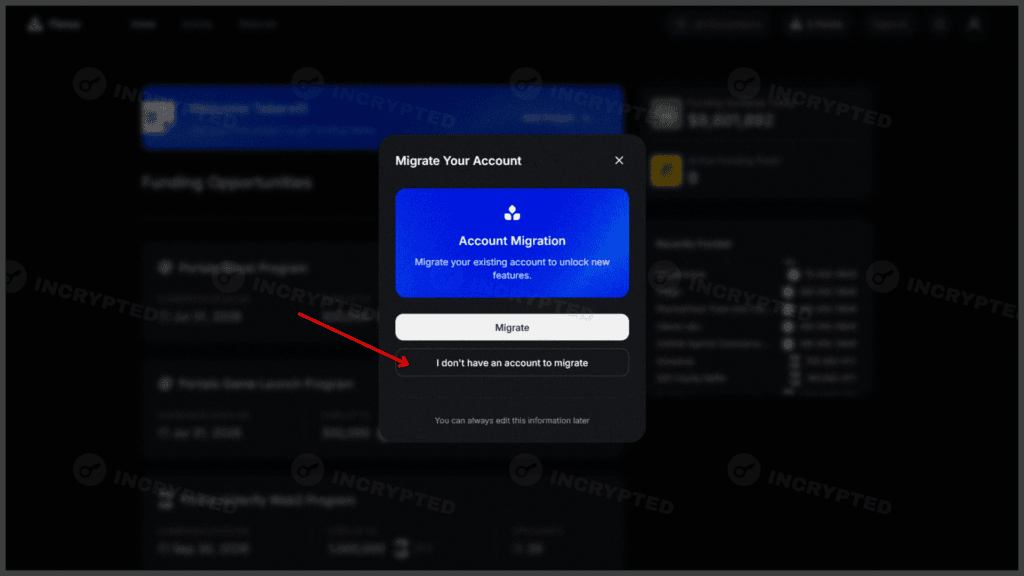
We are going through registration. Thrive.
- On the page, sign the manifesto at the bottom:
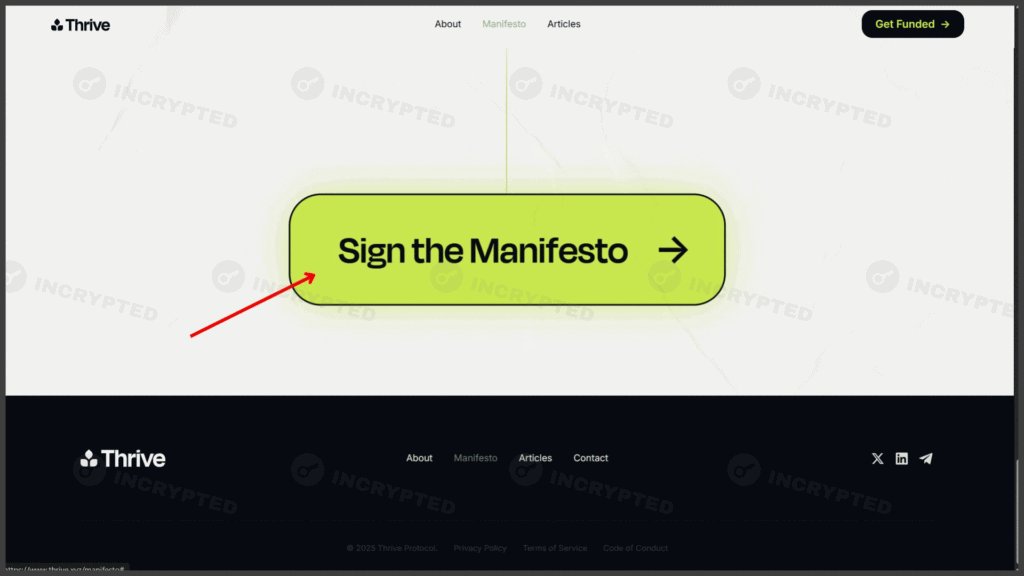
Signing the manifesto. Thrive.
- Read additional tasks on the page of the blog and earn points:
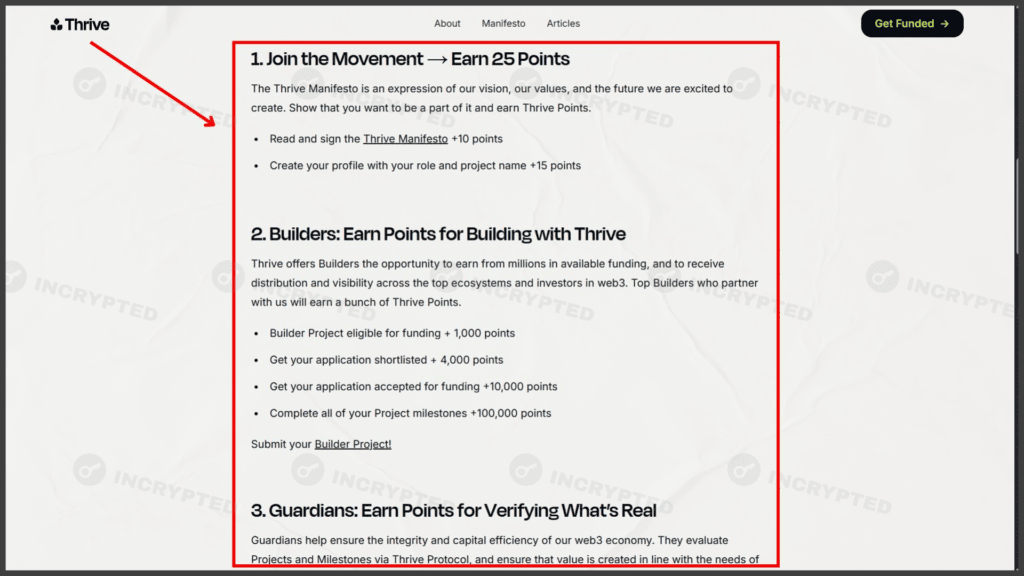
Additional tasks. Thrive.
At the time of writing, there is not much activity, and there is no information about investments. Points can be earned at three levels: as an ambassador, as a regular user, and as a project builder. We are also waiting for the launch of the main points program for everyone.
Follow the project on social media so you don’t miss any important updates.
Highlights:
- we perform tasks;
- farm points.
If you have any questions during the activities, you can ask them in our Telegram chat.
Useful links: Website | X
Disclaimer: The articles reposted on this site are sourced from public platforms and are provided for informational purposes only. They do not necessarily reflect the views of MEXC. All rights remain with the original authors. If you believe any content infringes on third-party rights, please contact
[email protected] for removal. MEXC makes no guarantees regarding the accuracy, completeness, or timeliness of the content and is not responsible for any actions taken based on the information provided. The content does not constitute financial, legal, or other professional advice, nor should it be considered a recommendation or endorsement by MEXC.
 We are going through registration. Thrive.
We are going through registration. Thrive.
 Signing the manifesto. Thrive.
Signing the manifesto. Thrive.
 Additional tasks. Thrive.
Additional tasks. Thrive.


